NIST 800-88 Hard Drive Destruction
NIST 800-88 sanitization guidelines are the new standard for information destruction. How to incorporate these guidelines into your computer recycling program.
Method | Verification | Reporting
NIST 800-88 Hard Drive Shredding
NIST 800-88 Guidelines for Media Sanitization is the technical standard for digital media data destruction. These guidelines lay out the methods, verification procedures, and reporting requirements for proper data destruction in compliance with data privacy laws.
Data privacy laws related to the healthcare, banking, consumer information, and credit industries all point to NIST 800-88 as best practices for data destruction. HIPAA and the Red Flags Rule specifically name NIST 800-88 as the standard procedure for secure information destruction. The 3 rules for compliance.
Destruction Method
Verification of Sanitization
Certificate of Destruction

NIST 800-88 recommends that holders of confidenital information consider using destruction devices listed on the National Security Agency (NSA) evaluated products list.
According to NIST 800-88 Guidelines for Media Sanitization, shredding hard drives is the most secure and compliant form of data destruction.
NIST 800-88 Documentation Requirement
The Certificate of Destruction is one of most important documents for your records. Information should include the date, method, personnel, witnesses and third party vendor.
The E-Waste Security COD, shown below, is the final step in larger Chain of Custody process. A sample NIST Certificate of Destruction is available.
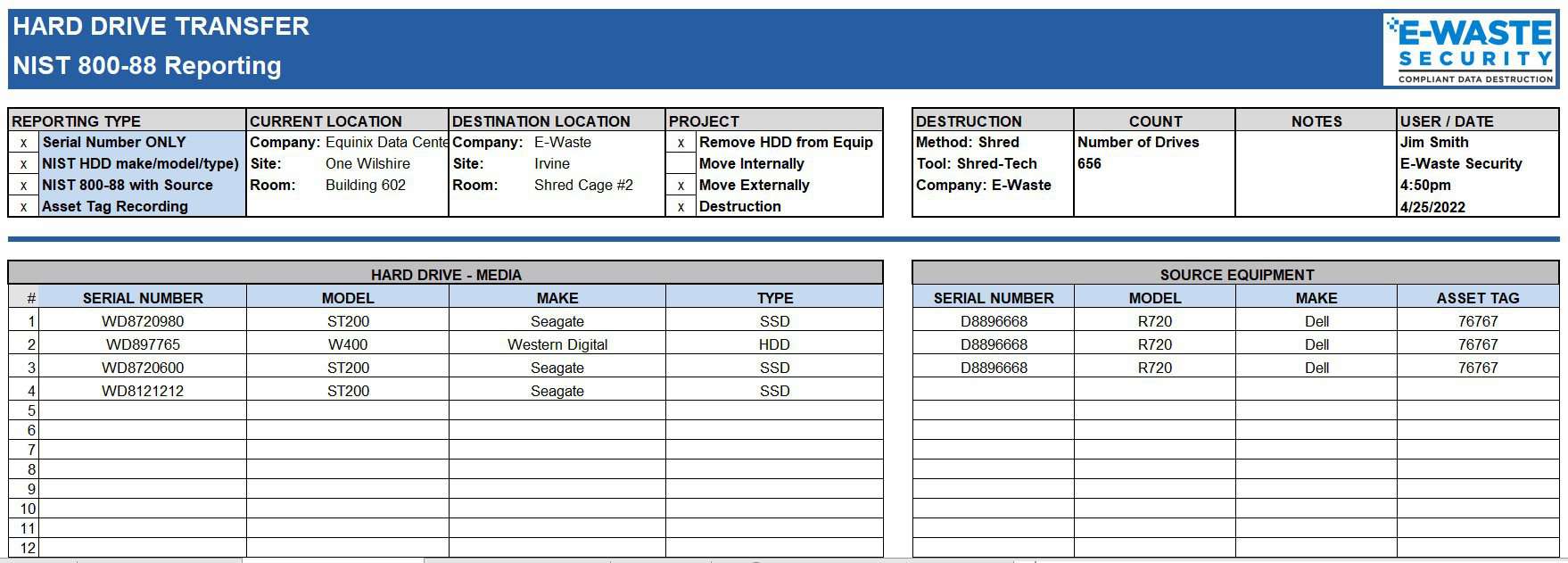

A NIST 800-88 Certificate of Destruction requires linking the hard drive or SSD to the parent computer or server. Details include make, model, serial number, and type. Below is a sample Certificate of Destruction of ours.
Many businesses and organizations must now have a written Identity Theft Prevention Program per the Federal Trade Commission’s Red Flags Rule. Conforming to NIST 800-88 guidelines requires proper documentation of data destruction, more commonly known as a Certificate of Destruction. Ask us about the difference between our standard Certificate of Destruction and a NIST certificate!
E-Waste Security offers a NIST 800-88 Certificate of Destruction to help you comply with NIST 800-88 documentation requirements.

NIST 800-88: Deciding on the Destruction Method
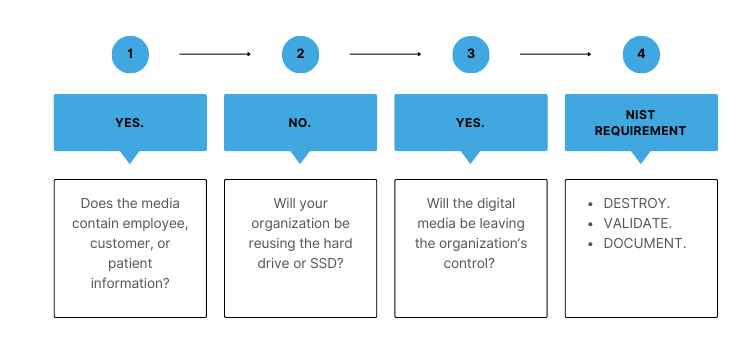
NIST 800-88 Data Destruction Decision
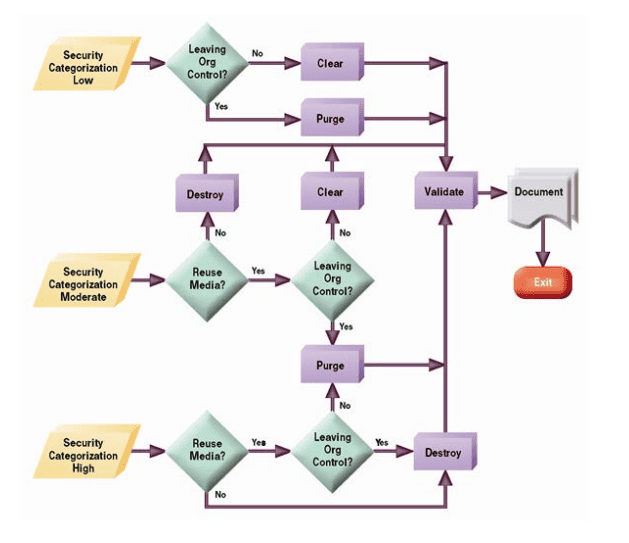
Compliance with NIST 800-88 data destruction requires organizations to make only two decisions. The first, and most important, decision is determining how critical the information is to the company, its employees, and its customers. The second is who will have access to the digital media after disposal.
Once those questions are answered, the NIST 800-88 decision tree states the method of digital media destruction.
Define Security Level
If the information became public, would it be detrimental or catastrophic to the company, employees, or customers?
In a practical sense, any loss of information would expose the company to fines, litigation costs, and reputational damage.
Control: Chain of Custody
Will the digital media leave your custody or control? Once a hard drive or SSD is given to a third party it is considered “out of your control”. It is irrelevant if the drive has been erased, wiped, or encrypted.
You and your organization are completely reliant on the vendor to protect the information.
Destruction Method
The NIST 800-88 data destruction decision tree is very clear; shred computer hard drives and SSDs before they leave your control.
According to NIST 800-88, shredding hard drives is the most secure and compliant form of data destruction





NIST 800-88: Hard Drive & SSD Destruction
Let us know if we can help with your project.
