Part 4 of 5: In this series, we’re exploring how to maintain compliance with the MPAA Content Security Best Practices during the decommissioning process. Part four takes a deeper look into the importance of tracking digital assets from the launch of the project through the certified destruction of the hard drives. To begin the series, MPAA Content Security: Media Destruction provided an overview of the guidelines and their impact on your entertainment industry business.
[cherry_hr]
 Post-production vendors in the entertainment industry have a significant responsibility when it comes to protecting their client’s assets. In a time when an endless amount of information is at consumers’ fingertips, there is a growing market for leaked movie footage, spoilers, and images. Because of this, all vendors in the entertainment industry must become hyper-vigilant about protecting content during the project and while decommissioning hard drives after the project is complete.
Post-production vendors in the entertainment industry have a significant responsibility when it comes to protecting their client’s assets. In a time when an endless amount of information is at consumers’ fingertips, there is a growing market for leaked movie footage, spoilers, and images. Because of this, all vendors in the entertainment industry must become hyper-vigilant about protecting content during the project and while decommissioning hard drives after the project is complete.
The Motion Picture Association of America, Inc. (MPAA) established the MPAA Content Security Best Practices to create an industry-wide baseline for securing physical and digital assets. A major point of discussion in these uniform guidelines involves asset management – or knowing where each asset is located, who has access to it, and when/how it was destroyed.
Overview of Asset Management for MPAA Content Security Best Practices
Sections PS 12.0 – PS 16.4 of the MPAA Content Security Best Practices discuss issues related to the topic of asset management. It begins with implementing an asset management system to track the movements of and access to proprietary content. This process includes creating barcodes or unique tracking identifiers for hard drives and storage devices that contain client assets and created media; maintaining detailed logs while the assets are in your control; and restricting access to protected content.
Despite protecting the clients’ content throughout the project, many post-production vendors make a crucial error by assuming their responsibility ends when the final product is delivered. The handling of data during the decommissioning and hard drive destruction process is just as important as the way it’s tracked earlier in the project.
Step 3 of the Content Disposal Process: Logging Your Assets
MPAA-compliant content disposal involves several essential steps, including:
1. Damaging, overwriting, or sanitizing hard drives that are ready for decommissioning (Step 1)
2. Securely storing those drives prior to certified hard drive destruction (Step 2)
Step 3 of the process outlines the importance of creating and maintaining an asset disposal log for at least 12 months after the completion of a project.
Section PS 16.2 of the MPAA Content Security Best Practices
Integrate the logging of asset disposal into the asset management process and include a final disposal record for all disposed assets in the disposal logs.
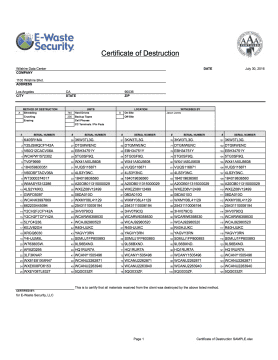 PS 16.2 is an essential step because your post-production studio remains fully liable for the content until you have a Certificate of Destruction from a reliable NAID-Certified Vendor. Additionally, all of the large film studios, such as CBS Studios and MGM, will audit their post-production vendors following a project to ensure compliance with MPAA Content Security Best Practices or with the studio-specific requirements. Failing to maintain compliant could mean serious penalties, including (but not limited to) losing any future contracts with the studio.
PS 16.2 is an essential step because your post-production studio remains fully liable for the content until you have a Certificate of Destruction from a reliable NAID-Certified Vendor. Additionally, all of the large film studios, such as CBS Studios and MGM, will audit their post-production vendors following a project to ensure compliance with MPAA Content Security Best Practices or with the studio-specific requirements. Failing to maintain compliant could mean serious penalties, including (but not limited to) losing any future contracts with the studio.
At E-Waste Security, we support our entertainment industry clients by providing detailed and compliant documentation of all destroyed assets, including serial numbers of each piece of equipment and the technique employed to destroy the data.
Learn How to Maintain Compliance with MPAA Content Security Best Practices
E-Waste Security is a hard drive destruction and IT asset disposition company based in Los Angeles, CA. Our onsite data destruction and hard drive shredding service is NAID Certified and compliant with PCI DSS, HIPAA, and GLBA. We provide full-service IT Asset Disposition (ITAD) services including the purchase, removal, and recycling of computer equipment to provide our clients with a convenient solution for their decommissioning projects.
Contact Us Today for a quote.
